Both authentication and authorization are important for data security in an online system. They protect the key components of the infrastructure so that the services provided can be used safely. Although terms are often used in the same context and with the same tool, each term’s meaning is different.
- Authentication is used to verify that users are who they say they are. Once verified,
- Authorization allows access to different levels of information and functions depending on the rules established for each type of user.
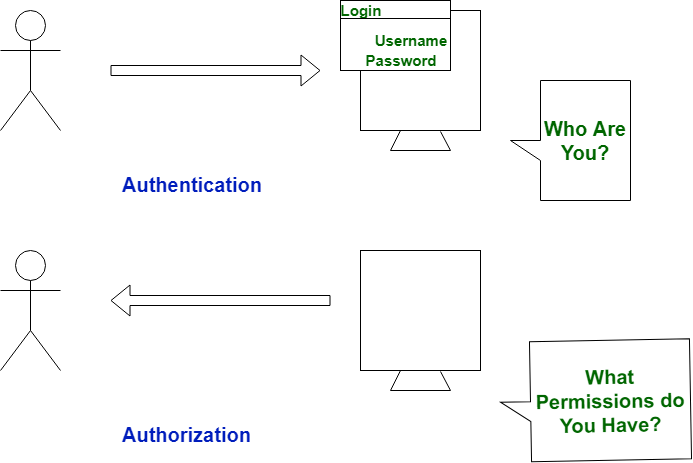 Image Source: geeksforgeeks
Image Source: geeksforgeeks
Key differences between authentication and authorization:
| Authentication | Authorization |
|---|---|
| - Authentication confirms the user’s identity. | - Authorization protects the system by only allowing users to access certain resources. |
| - Authentication requires user input such as passwords, one-time pins, or biometric information. | - Authorization to access certain website areas is set and regulated by the organization. |
| - Access cannot be granted without first verifying the identity of the requestor. | - After a user is authenticated, authorization can take place. |
| - Authentication is visible and partially changeable by users. | - Authorization settings is not visible at the user end. |
| - e.g. After verifying their identity, employees can access an HR application with sensitive information like payment history, vacation time, and 401K data. | - e.g. Once their level of access is authorized, employees can access different data levels in a HR systbased on the organization’s permissions. |
| Popular Authentication Mechanisms: Password,2FA/MFA, SSO | Popular Authentication Mechanisms: RBAC, JWT, SAML, OpenID and OAuth |
